
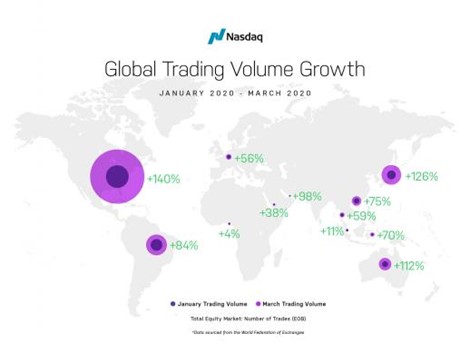
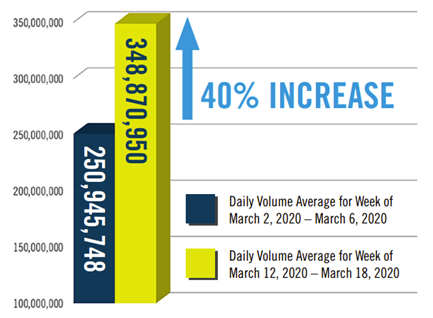
Operationally speaking, 2020 has been a banner year for exchanges and financial market infrastructures. The World Federation of Exchanges (WFE) said value and volume traded worldwide set records in the first half, rising nearly 50% from a year earlier. The peaks in volumes and volatility were handled with nary a hitch. (A few exceptions were small, emerging-market bourses that took themselves off-line while global volumes were spiking early in the year.)
“There were a lot of discussions around whether or not we should consider closing the markets, for a period of a day or more, to allow calm to try to reestablish itself,” Nasdaq president and chief executive officer Adena Friedman noted during a recent online event. “However, we are here to provide liquidity to investors and companies, and if we had done anything to disrupt that flow of liquidity, I feel it would have created a huge trust issue within the capital markets in the United States and elsewhere.”
Meanwhile, like virtually everything else in the increasingly digitized pandemic-era economy, securities trading was contending with an upsurge of cyber attacks and criminality. In May, the WFE, which represents 250 market infrastructure providers, published an update on cybersecurity, saying it “consistently remains in the top quartile of WFE regular surveys of membership priorities and focus.” Stated CEO Nandini Sukumar: “As markets and businesses have grown electronic, market infrastructures now devote a greater amount of resource and time to ensure cyber resilience than ever before. When the current worldwide pandemic situation, hopefully, lessens and countries and companies implement measured return-to-work procedures, WFE members recognize there will be a new normal operating environment for all in which such measures must continually be monitored, reviewed and implemented to protect against future threats.”
For all the awareness, contingency planning and preparation - a 2016 report by the International Organization of Securities Commissions (IOSCO) on cybersecurity in securities markets is one of a number of extant regulatory documents - cyber threats are constantly looming, and one that struck in New Zealand this summer sent shudders through the global market community.
“Well-Resourced and Sophisticated”
In late August, the exchange operator NZX was bombarded by a volumetric distributed denial of service (DDoS) attack, a type that information security officers have long been alert to. It is designed to overwhelm a server or network with incoming traffic, greatly limiting if not disabling its responsiveness.
The DDoS did not hit NZX's core infrastructure, which includes X-Stream, a Nasdaq-developed trading platform. It directly affected the NZX.com website and a system that NZX relies on for public announcements and real-time disclosures, without which the stock market cannot properly operate. The exchange was down for all or part of five days, working around the problem with security technology from Akamai Technologies, as NZ Herald reported.
The attacks were “among the largest, most well-resourced and sophisticated” ever seen in New Zealand, the exchange company's chief executive, Mark Peterson, said in a statement. By the end of September, NZX chief information officer David Godfrey had announced his resignation.
Economic Costs
Any such incident naturally raises questions about the source of the attack, the likelihood that others will be targeted, the state of defenders' preparedness, and potential systemic consequences. The markets, and confidence in their systems and reliability, are critical to capital formation and economic growth. Isolated glitches may be manageable and their damage containable. Crashes that are more severe or capable of spreading contagion could be disastrous.
The report of the U.S. Cyberspace Solarium Commission, a bipartisan blueprint for national cyber defense issued last March, included among its recommendations “Continuity of the Economy planning in consultation with the private sector.” This process, the report said, “should emphasize the importance of developing plans to mitigate the consequences of successful cyber attacks” on stock exchanges, wholesale payment systems, power distribution, telecommunications and other sectors that could result in cascading or catastrophic economic effects if brought low.
The leading market infrastructures that proved their mettle through the volatile swings of 2020 are part of a global financial industry that hackers have long regarded as a prime, deep-pocketed target, and is believed to be in the crosshairs of nation-states or surrogates seeking geopolitical advantage.
New Zealand, though not a superpower, is a member of the geopolitically significant Five Eyes intelligence alliance, along with Australia, Canada, the United Kingdom and United States. All have stock exchanges that rank among the world's 20 largest in total capitalization - except New Zealand. It may just have been the lowest-hanging fruit, from an attacker's perspective.

Ilia Kolochenko, founder and CEO of application security company ImmuniWeb, considered a scenario in which NZX was not the primary target, saying, “This may be a rehearsal of a major attack targeting Nasdaq or LSE [London Stock Exchange] amid the craziness going on the global stock markets.”
Jerry Perullo, chief information security officer of Intercontinental Exchange (ICE), parent of the New York Stock Exchange, revealed during a panel discussion at the Sibos conference in early October that eight stock exchanges were attacked around the same time.
Crime That Pays
It may also be a matter of timing. John P. Carlin, a former assistant attorney general for the U.S. Department of Justice's National Security Division and chief of staff to then-FBI Director Robert Mueller, now with the law firm Morrison & Foerster, points out that the DDoS “business” - like ransomware, with which it is often associated - is thriving. The botnets available to perpetrators are cheaper than ever to purchase and unleash. Those with nefarious intent - groups in Russia, China, Iran and North Korea are “usual suspects” - are difficult to identify, easily disguised and rarely brought to justice.
So there are more attacks - Nexusguard said DDoS attacks in the first quarter of 2020 increased 542% from the previous quarter - and NZX lacked the protection of products from the likes of Akamai and Cloudflare that the larger exchanges routinely rely on. Assessing what went wrong at NZX, IT security consultant Daniel Ayers in a video interview pointed to inadequate design, overconfidence, and what turned out to be a “low-probability, high-impact risk event.”
Carlin and other observers therefore stop short of deeming the NZX incident a singular wake-up call for other markets that are effectively scanning the cyber landscape, sharing threat intelligence through organizations like the Financial Services Information Sharing and Analysis Center (FS-ISAC) - of which ICE's Jerry Perullo is chairman - and engaging in what one senior information security executive in the industry terms “complex risk analysis.”
“There was a lot of chatter” when the NZX news broke, says the security officer, asking not to be identified by name. But most were reassured by the fact that they had “DDoS protections in place.”
It will be a wake-up call for those in any industry that need to bolster those protections, particularly in the heated COVID-19 environment. “You never want to let a crisis go to waste,” says Randy Watkins, chief technology officer of Critical Start, a provider of managed detection and response services. “This brings attention to the issue and can help CISOs [chief information security officers] with their budgets.”
Recommended Actions
“Enroll in a denial-of-service mitigation service that detects abnormal traffic flows and redirects traffic away from your network,” the FBI recommended in a July alert, Cyber Actors Exploiting Built-In Network Protocols to Carry Out Larger, More Destructive Distributed Denial of Service Attacks.
Still, DDoS mitigation must continue to evolve as the threat proliferates and mutates. Kolochenko of ImmuniWeb says that the falling prices of bots will probably make these attacks “even more affordable. When millions of devices suddenly start a massive attack, it's a question of network capacity, not really network security. We witnessed many examples in the past, when even the largest DDoS protection companies ceased protecting some of their clients under exceptionally large DDoS and gave up.”
He recommends regular auditing of web applications and application programming interfaces (APIs) for “business logic and architectural security flaws” that could facilitate a DDoS attack.
“Going forward, we see the evolution of DDoS spreading to SaaS [software as a service] via account lockouts and takeover,” warns Maor Bin, co-founder and CEO of Adaptive Shield. “Instead of bringing the servers to their knees, attackers are starting to bring end users to their knees.”
Other Glitches
Such are the jitters about cyber attacks that when the Tokyo Stock Exchange suffered an outage on October 1, and Mexico's Bolsa Mexicana de Valores halted trading at midday on October 9, officials in both cases were quick to announce that hacking was not the cause. The TSE did have a disabling hardware failure, and BMV blamed a trading-engine disconnect on a technology provider. By contrast, there was no ambiguity on October 12 when the Hong Kong Stock Exchange closed because of a typhoon. On the same day, the major Indian markets BSE and National Stock Exchange kept functioning through a power outage, Bloomberg reported.
On October 19, stock and derivatives trading on Euronext was halted for three hours because of a middleware breakdown.
Indeed, securities markets have long been fighting off system and network fragility. A chronology of incidents compiled recently by John McCrank of Reuters began with squirrels chewing through Nasdaq power lines in Connecticut in 1994 (after a similar 1987 event), followed by the May 2010 “flash crash” and breakdowns in 2012 that marred the IPOs of Bats Global Markets (now part of Cboe Global Markets) and Facebook.
In a 2018 report on market infrastructures and market integrity, Oliver Wyman and the World Federation of Exchanges described an industry looking to expand its range of services, build new technological capabilities, respond to changing credit and liquidity risk management needs, and manage “new non-financial risks, such as cyber risk as well as a broader set of market risks stemming from macroeconomic and geopolitical developments [that] need to be accommodated.” They estimated that market participants and infrastructures would have to invest $3 billion to $4 billion over five years on an agenda to ensure improved market integrity.
“Market integrity is closely related to the management of systemic risk,” Oliver Wyman and WFE said. “When systemic risks materialize, markets may suffer from pro-cyclical stress, become disorderly, and/or cease to effectively match buyers and sellers. Conversely, an absence of transparency or a lack of confidence in the integrity of markets may produce systemic stress.”
Operational reliability and resilience - along with cybersecurity vigilance - remains no less urgent and consequential.