Eyeing perceived gaps and mounting complexities in third-party risk management, the Shared Assessments Program is offering a comprehensive framework and guide to promote best practices in the field.
The announcement of the Third Party Risk Management (TPRM) Framework in June followed the April release of the Shared Assessments-Protiviti annual Vendor Risk Management Benchmark Study , which concluded that "to varying degrees across all industries, [vendor risk] programs are barely able to keep up with the fast pace of change in the external environment." (See Vendor Risk Programs 'Running to Stay in Place' )
Further indicating the urgency of assistance and guidance in dealing with this category of risk, the cybersecurity professional association (ISC)² said in June that half of the large-enterprise respondents to its Securing the Partner Ecosystem survey viewed its third-party partners as cybersecurity risks.
Sixty-four percent of large enterprises outsourced at least 26% of their daily business tasks, which requires them to allow third-party access to their data. But (ISC)² found that smaller businesses were not necessarily the weakest link in supply chains. While 34% of large enterprises said they have been surprised by the broad level of access that third-party providers granted to networks and data, 39% of small businesses expressed the same surprise about the access they were granted when providing services to larger partners.
"This research highlights the fact that building a strong cybersecurity culture and subscribing to the right best practices can help organizations of any size maximize their security effectiveness," said (ISC)² chief operating officer Wesley Simpson. "It's a good reminder that in any partner ecosystem, the responsibility for protecting systems and data needs to be a collaborative effort, and multiple fail safes should be deployed to maintain a vigilant and secure environment."
Beginning with the Basics
The need to be agile and proactive was top of mind in developing the TPRM Framework, said Gary Roboff, who led development of the framework and is senior adviser of the Santa Fe Group, managing agent of the Shared Assessments Program. The organization has a risk practitioner membership and two certifications: Certified Third Party Risk Professional (CTPRP) and Certified Third Party Risk Assessor (CTPRA).
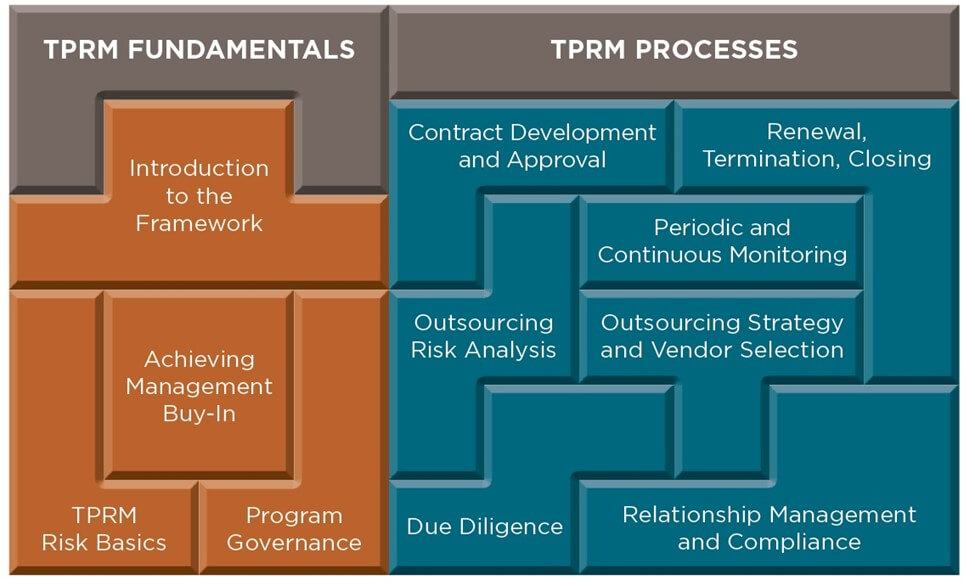
The first two modules of the framework - an introduction and Risk Management Basics (referred to as module 1) - were available to members as of mid-June. The offering is designed to be useful for board members, C-level executives and both beginning and advanced practitioners.
Risk basics cover such concepts as inherent and residual risk, risk appetite statements and frameworks, risk tolerance metrics, and process factors to be considered when building a TPRM program.
Modules 2 through 10, each falling within the categories TPRM Fundamentals or TPRM Processes, have been outlined (see image). The next two coming under fundamentals, for example, are Achieving Management Buy-In and TPRM Program Governance.
Roboff said it amounts to the broadest available overview of third-party risk management, at a time when oversight of outsourcing processes and relationships has become increasingly critical.
"Knowledge and Practical Skills"
"There has been a significant increase in third-party-related vulnerabilities in recent years, which has in turn resulted in increased demand for Shared Assessments Program resources, so the development of the TPRM Framework is needed now more than ever," Catherine Allen, chairman and CEO of Shared Assessments and of Santa Fe Group, said in a statement.
"Increasing third-party risks, together with new and changing regulatory mandates, require a new approach for providing the knowledge and practical skills necessary to help organizations more effectively manage third party risk," Allen added. The framework "represents a critical and effective step forward to help organizations move toward best risk management practices."
Said Roboff: "The TPRM Framework is designed to provide guidance for organizations seeking to develop, optimize and manage third-party-risk best practices. The framework also provides guidance about how to implement meaningful incremental improvements in TPRM practice maturity in organizations where resources may be constrained. Resource allocation is a significant obstacle for almost every organization in the current environment."
Partnership with Panorays
Panorays, a provider of technology for third-party security management, on July 16 announced a collaboration with Shared Assessments. Panorays' multi-industry customer base will be able to gain access, and receive evaluation responses within days, to the Standardized Information Gathering (SIG) questionnaire to assess their third-party cybersecurity risk. SIG is updated annually by the Shared Assessments member community to reflect current security and privacy concerns, regulatory changes and best-practice trends in third-party security.
"SIG is reflective of the knowledge and experience of hundreds of member organizations. Panorays is delighted to be able to join this community and contribute to the continued development of third-party security best-practice guidelines," said Dov Goldman, Panorays director of risk and compliance. The SIG platform "eliminates the need for manual questionnaires, automates the security evaluation of the company's cyber posture and dramatically speeds up the third-party vetting process."
Catherine Allen of Shared Assessments said that Panorays' adoption of SIG and contribution to the process "is working to create standard assessments that are reliable, relevant and efficient."
Common Practices
(ISC)², which is responsible for the Certified Information Systems Security Professional (CISSP) certification, said that a third of the 709 IT and cybersecurity decision-makers who took its survey in November had suffered a breach through a vendor; 54% blamed a large partner, and 46% a small partner.
Not discounting smaller enterprises' risk management capabilities or the talent they employ, the report said, "It's not always the size of the target, but the company's adherence to cybersecurity best practices, that matters most in cyber defense."
Nearly all in the poll were confident or very confident that they can protect their data if a vendor were breached. The high level of confidence among those from large enterprises "seems misplaced, as the study shows that more than half of small businesses (54%) have been surprised by some of their enterprise clients' inadequate security practices, and 53% have notified large clients of security vulnerabilities they've discovered," (ISC)² said.
For both sets of respondents, the top three best practices for protecting networks and data were the same: Regular automatic anti-virus and anti-malware scans; blocking access to known malicious IP addresses through firewall configuration; and strong email filters to prevent phishing.