
Times get tough, life eventually settles to a new normal and we plow on. It's now time to rethink how we should work, rather than continue to navigate within the old construct. Looking ahead, in the aftermath of the global pandemic, nothing less than organizational survival will be at stake.
Integrated risk management (IRM) is one clear path forward. It binds the way groups within a company interact with each other, their internal stakeholders and external support.

In a financial institution, we talk about interactions across the three lines of defense. In a corporation, we address the interactions across sales, suppliers, operations and support functions. In a non-profit, we talk about the work between funders, operations and support.
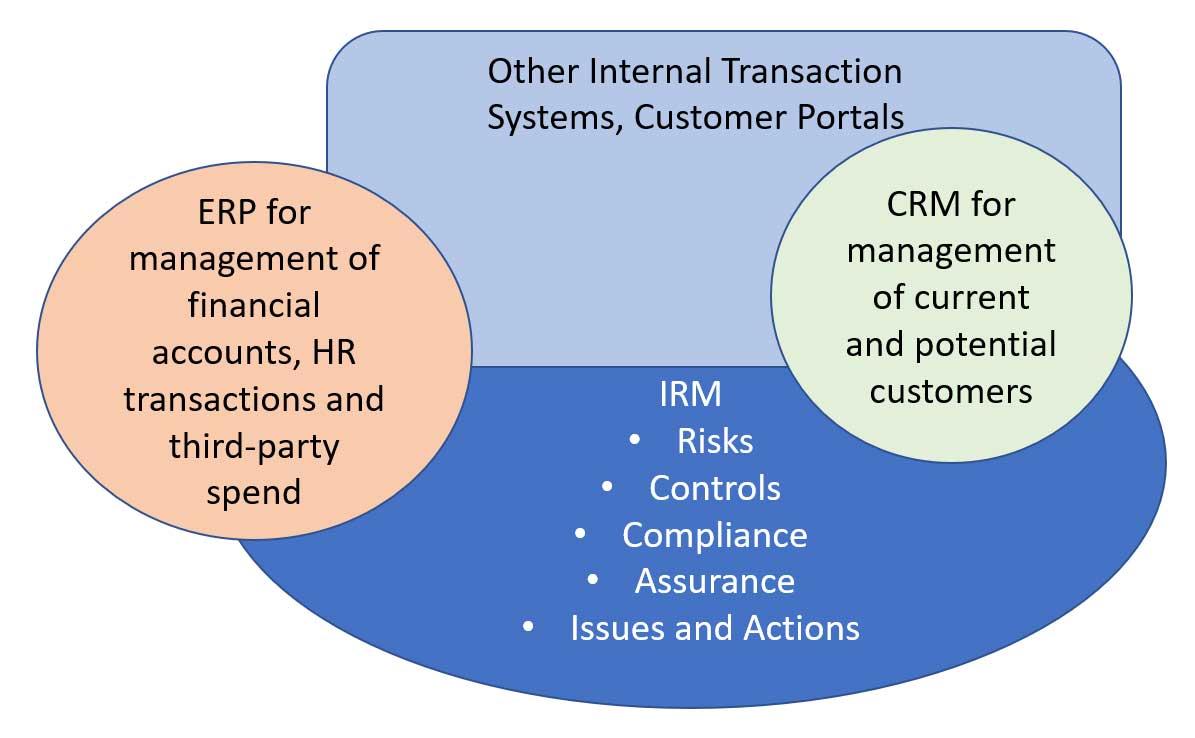
In all cases, IRM is a critical aspect of an organization's enterprise architecture, and the fabric that binds internal and external stakeholders across all these activities. Figure 1 provides a high-level overview of an enterprise business architecture, including transaction systems, customer portals, CRM, ERP and the IRM capabilities that bind the collaboration.
Figure 1: Target Enterprise Architecture
An organizational system is characterized by its culture, or standards of individual behavior. On one extreme, behaviors within an organization can be siloed, led by warrior kings climbing their hill.
Alternatively, the culture may encourage collaboration across employees and third parties. Most organizations have leadership approaches somewhere in the middle.
The IRM endgame is to remove the silos that inhibit collaboration and agility, via digitization of internal support processes. But there are steps that must be taken first to improve processes.
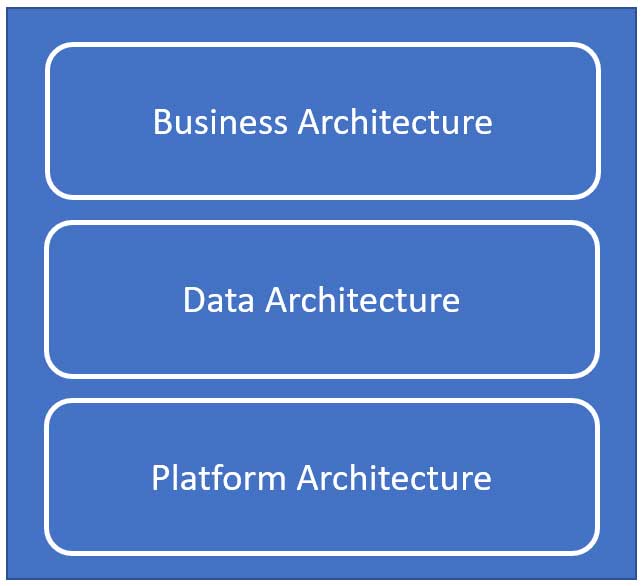
IRM Platform Architecture: The Glue that Binds Collaboration
IRM describes processes, data and points of integration. This article will focus on the third component of Figure 2 - IRM platform architecture.
Figure 2: IRM High-Level Architecture
Nothing about IRM is necessarily technology dependent - but technology can help achieve process efficiencies, data integrity and collaboration. Where humans are the weakest link, automation can help achieve overhead benefits and cultural collaboration. Figure 3 shows the IRM platform architecture, including users, capabilities and data.
Figure 3: Diagram of an IRM Platform Architecture
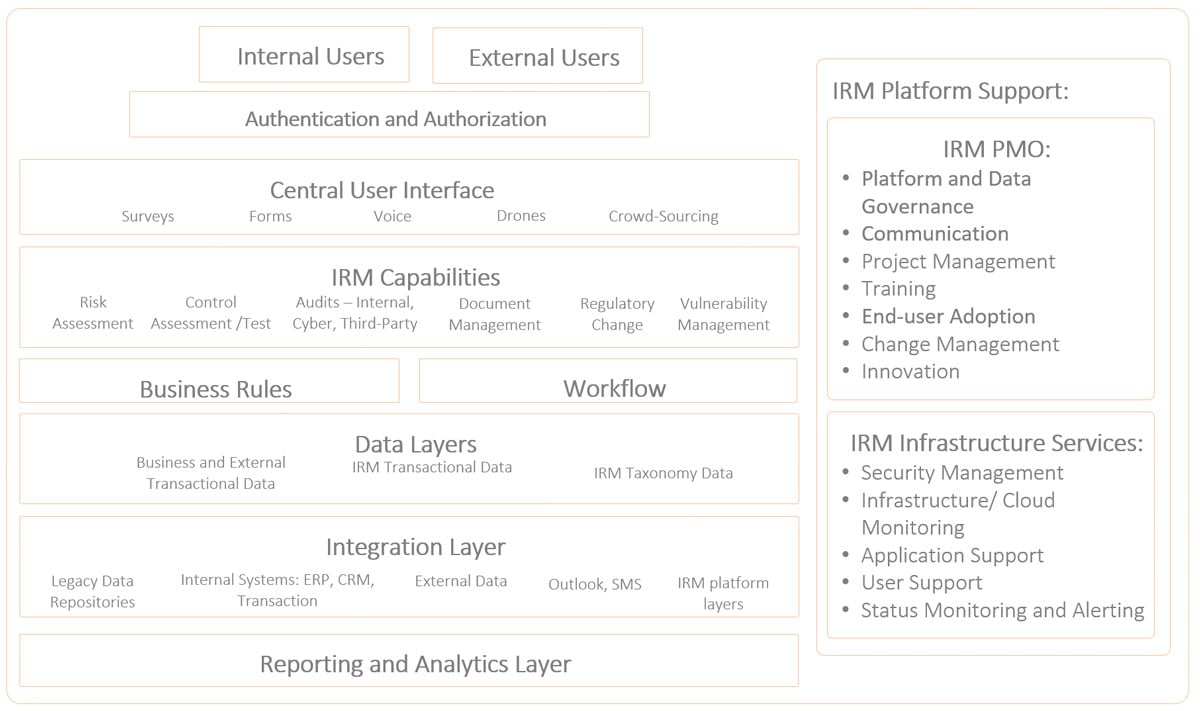
A lesson from over a decade of GRC technology and process implementation is that the “layers” in your IRM platform should be separated, yet tightly integrated. Let's now take a look at key layers of a modular IRM architecture, which allows for “plug and play” of the best-of-breed capability.
Users
Users will be full- and part-time employees, third parties and customers. It is important that we are clear about the roles, objectives and benefits for each group.
Authentication and Authorization
Users will need to be authenticated and authorized before inputting data and accessing results. Authentication identifies a person with an ID and password. Authorization provides permissions to ensure people have access to capabilities needed by their role. Open access democratizes and allows broader leverage of the data.
Central User Interface
This is the approach to how we get data into the IRM platform. Automated tools enable extraction of data that's needed. For example, TurboTax allows you to complete an income tax return without ever seeing the form. But traditional forms can be also useful, allowing direct input of data, typically aligned with what is needed for business rules, calculations and reporting.
Other methods of data input include mobile devices, crowd sourcing and drones. Drones enable remote asset reconnaissance. Mobile devices allow a person to take pictures, capture GPS coordinates and record voice. Crowdsourcing enables identification of any issue, at any time.
Think about it - when you raise your hand, you can ask a question or provide an answer. How can we encourage employees and third parties to raise their hands? There's a need for innovation here.
IRM Capabilities
The IRM functionality required will be determined by an organization's strategy and footprint. Each function should allow for data input, business rules, calculations and workflow.
It all starts with risk assessment, which can be top-down or bottom-up. The goal is to understand inherent and residual risk levels, the risk factors that drive inherent risk and the rating scales that normalize importance of an issue.
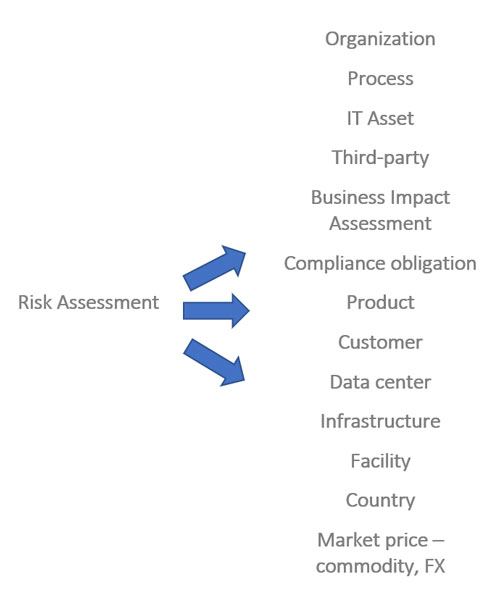
Figure 4 provides examples of the types of risk assessments performed to help an organization see through its windshield. An approach to bottom-up risk assessment is described in a prior CRO Outlook column.
Figure 4: Risk Assessment Types
Aside from risk assessment, what are some of the other functions of an IRM platform? Let's take a look:
Control Assessment and Testing
Controls ensure a business process is performed in the way intended. There are often hundreds of controls to ensure one end-to-end business process works as expected.
Some of the controls may be required by law (e.g., SOX, data privacy), and others are management directed to mitigate risks. In managing each control, a user or machine can perform the control activity, and a control assessor can test or assess its efficacy and design.
The assessor should document the results of control tests or assessments, capture non-compliance issues, and certify the effectiveness of the controls.
Audit and Assurance
In addition to the control assessments, many organizations require an independent review of the adequacy of the control environment. Audits may be performed by an internal team or a third-party. Auditors generally scope an exam, schedule their work, perform their work, record results, compile a report of findings, deliver the results and track agreed actions.
Obligation Management
Every organization manages some type of repository of its obligations to lenders, regulators, multinational, state and local government and management. Some requirements may have multiple sources.
For example, data privacy requires compliance with legislation and regulation, such as GDPR and CCPA, and industry standards, such as NIST, PCI-DSS and ISO 27001. Internal policy requirements, moreover, must also be met.
Obligation Change Management
No compliance obligation stays constant, and a company must have a way of managing change. Each obligation change may lead to adjustments in business strategy and controls.
Document Management
Policies are the way management communicates to employees and external stakeholders its objectives, as well as how each should be fulfilled. They can be supported by additional documents, such as procedures and reference materials.
Documents must be deliberately managed to ensure access and search; creation; modification; mapping to risks; controls and obligations; and reviews and approval. In addition, many organizations seek to track exceptions and attestations to policy content by employees. Discovery may be required when things go wrong.
Regulator Engagement Management
Local or federal regulators may wish to review policies or controls. A third-party review may be directed by a customer.
Threat and Vulnerability Management
When a business is digitized and connected to an external network, business processes can be exposed to cyber risks. Many software companies make available possible threats based on software weaknesses they have identified.
Microsoft, for example, regularly publishes possible cyber weaknesses in its Office 365 suite of applications. Vulnerabilities are the threats that have happened based on a company's internal diagnostics.
Quality, or Nonconformance, Management
Manufacturers seek to test how much a product or service deviates from its specification or policy. The organization must log the nonconformance; a subsequent review and investigation may lead to corrective actions.
Operational Resilience and Business Continuity
Continued errors and systemic risks ensure that an organization's response to an event is at least as critical as its controls. For its critical economic functions, an organization will seek to understand the potential internal and external risks, define tolerances and run scenarios.
Metrics
Only what is measured can be managed. The alternative to measurement is hope - rarely a basis for survival. Thresholds can trigger actions.
Business Rules
To instruct workflow or calculation, logical rules must be applied consistently. The rules link a capability with one or more data sources, ultimately yielding analytics.
Data Layers
In a prior CRO Outlook column, we explored the IRM data architecture across business and external transaction data, transactional data and taxonomy data.
Event, Case, Incident, Corrective Action and Issue Management
In addition to internal screw-ups (events), culture deviations (cases) and external incidents, each of the capabilities above will give rise to issues. All should lead to desired actions that reduce a risk or shore up compliance. Action or inaction describes a company's governance.
Other Considerations
Data integrity is virtually impossible to achieve when IRM processes are manual. Automated data input checks and workflow approvals systematically improve data quality.
Core risk management processes should be standardized. Companies can't scale when daily management is case-by-case.
Modular and future-proofed tools can help avoid platform obsolescence. Plug and play capability layers allow innovation and an ability to leverage OpenSource innovations.
However, even the best software will reach end-of-life in five years or less. Upgrades and enhancements must be sought continuously.
The best applications can become shelf-ware when they are too rigid and are not supported with the right training and communication. The best cultural and technology systems are gamified and fun.
Parting Thoughts: Rethinking How We Work
Admittedly, it's hard to turn a global pandemic into an opportunity. The real economy will be fundamentally different when we re-emerge. The same is true for the companies that support it.
We have heard that we should never let a good crisis go to waste. Sometimes, transition works best when it is underpinned by duress. This is when the industrious keep their heads down and lead the change.
An IRM platform is the single biggest infrastructure change for driving sustainability, through acknowledged risk-taking and a coordinated response. Risk managers have built a strong foundation; now is the time to lead the transition.
Brenda Boultwood is an independent risk management consultant. She is the former senior vice president and chief risk officer at Constellation Energy, and has served as a board member at both the Committee of Chief Risk Officers (CCRO) and GARP. Previously, she was a senior vice president of industry solutions at MetricStream, where she was responsible for a portfolio of key industry verticals, including energy and utilities, federal agencies, strategic banking and financial services. Before that, she worked in a number of risk management, business roles and as the global head of strategy, Alternative Investment Services, at JPMorgan Chase, where she developed the strategy for the company's hedge fund services, private equity fund services, leveraged loan services and global derivative services. She currently serves on the board of directors at the Anne Arundel Workforce Development Corporation.