
The “systemically important” label, attached to an elite group of banks as a result of post-financial-crisis regulatory reforms, may soon be applicable to U.S. critical-infrastructure industries in addition to finance.
A proposal within the National Defense Authorization Act (NDAA) for 2023, which is on the Senate calendar after passage by the House in July, would define systemically important entities, or SIEs, for purposes of strengthening cybersecurity standards and information sharing under the aegis of the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA).
The measure grew out of a recommendation in the 2020 Cyberspace Solarium Commission report to “codify the concept of systemically important critical infrastructure.” It is championed by commission member Jim Langevin, a soon-to-retire Democratic representative from Rhode Island, and was one of the “remaining priorities” – those not incorporated in previous legislation – enumerated in the commission’s August 2021 annual report on implementation.
Congressman Jim Langevin
“In the nearly 22 years that I’ve served in Congress, we have come a long way in cyberspace,” said Langevin. “When I was elected in 2000, nobody was talking about cybersecurity.” The pending NDAA “makes historic strides to protect Americans and our allies in cyberspace.”
Financial Industry Precedent
The SIE proposal may be seen as an adaptation of the concept of systemic importance as it has played out in financial services, where designated large institutions are subjected to a prescribed or bespoke level of capital adequacy and other supervisory specifications.
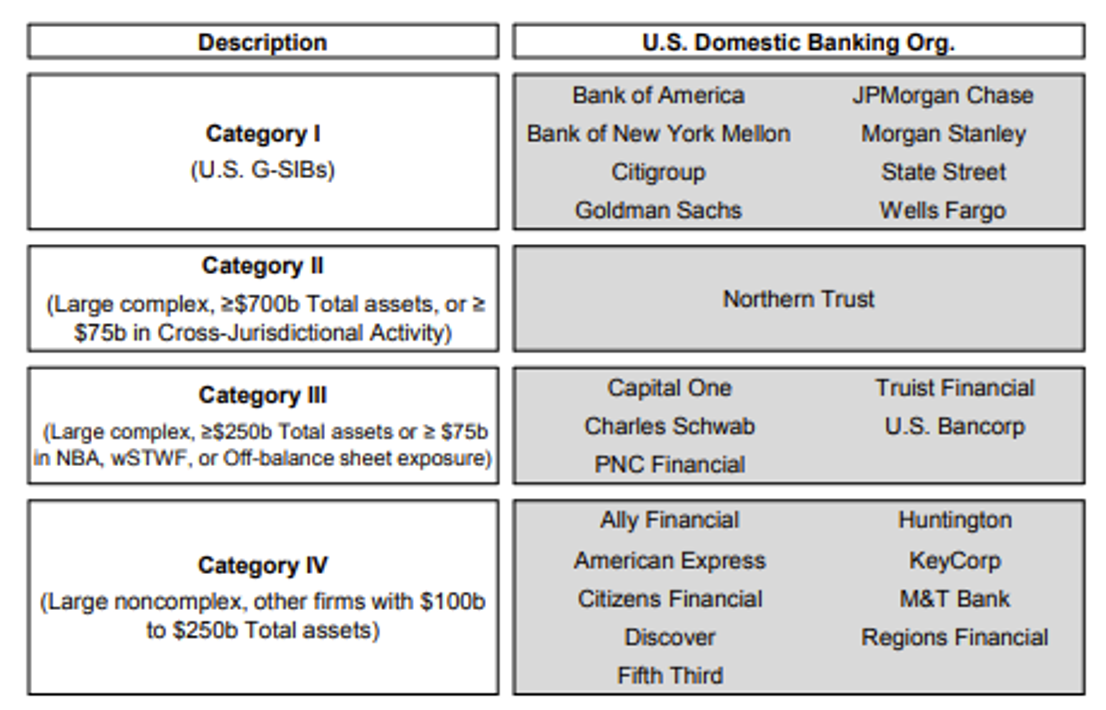
Systemically important U.S. banks, as shown in the Financial Stability Oversight Council 2021 Annual Report. The eight in Category I are on the Financial Stability Board’s international list of 30 global systemically important banks (G-SIBs).
Langevin called for an “interagency council” for coordination of critical infrastructure cybersecurity policy. A related provision would establish a CISA Office of Cybersecurity Statistics. Its mission to aggregate, analyze and disseminate relevant cyber incident data would roughly parallel that of the U.S. Treasury Office of Financial Research, which was created by the Dodd-Frank Act of 2010 to support the threat monitoring of the interagency Financial Stability Oversight Council.
The proposed, broad definition of SIEs goes well beyond the FSOC’s financial industry purview and its past deliberations over whether to include insurance companies and other nonbanks.
Not on Board
Yet opposition to the cyber regulatory initiative is coming from the banking sector.
Two leading trade groups, the American Bankers Association (ABA) and Bank Policy Institute (BPI), asserted in a July 29 letter to leaders of two Senate committees that banks participate in some of the most mature and effective, sector-specific threat intelligence programs. Those banks would now be “adding yet another layer of reporting to a different set of agencies with different standards [that] would detract significantly from financial institutions’ essential work defending against cyber threats.”
Another beef is with requirements to share with CISA “sensitive and extensive” information, such as details on supply-chain risk management practices and other external dependencies, which “could expose firms to risk if it is inappropriately disclosed or stolen in a breach.”
It remains to be seen whether the controversy escalates before the Senate votes. A proposal in the House earlier this year from John Katko, Republican of New York, ran up against what Nextgov reported to be a “partisan rift.” Langevin said Katko’s bill lacked the specificity of the “Solarium Commission’s vision.” Representative Yvette Clarke, a New York Democrat and chair of the Homeland Security Committee’s cybersecurity, infrastructure protection and innovation subcommittee, said the “benefits and burdens” of prospective systemically important companies were not sufficiently studied.
“National Critical Functions”
Besides Representative Langevin and others in the majority that voted for the NDAA, SIE designation has been supported in principle by Jen Easterly, CISA’s director since July 2021. A retired Army intelligence and cyber operations officer and former head of firm resilience at Morgan Stanley, which is a global systemically important bank (G-SIB), Easterly revealed last November that the agency was “already thinking through the model,” pending authorizing legislation.
Entity classifications would be “based on economic centrality, network centrality and logical dominance in the national critical functions,” Easterly said, according to an ExecutiveGov report.
CISA Director Jen Easterly
The Cyber Incident Reporting for Critical Infrastructure Act of 2022, which sets timeframes for prompt reporting to CISA, was signed into law by President Joe Biden in March, amid heightened concern about attacks emanating from Russia’s invasion of Ukraine.
That legislation had Easterly’s support for filling “critical information gaps,” though Justice Department officials said it was flawed, Sidley Austin LLP noted. The act’s intent, the law firm explained, was to “provide the federal government with a better understanding of the nation’s cyber threats and facilitate a coordinated national response to ransomware attacks.”
It also sought to improve on the state of voluntary information sharing, which was a Cyberspace Solarium Commission objective and is coordinated by sectoral bodies like the Financial Services Information Sharing and Analysis Center (FS-ISAC). The ABA-BPI letter called attention to significant industry commitments to FS-ISAC as well as “the Financial Services Sector Coordinating Council and the Analysis and Resilience Center for Systemic Risk – organizations that work to improve information sharing and readiness across financial firms and between critical infrastructure sectors.”
While expressing some misgivings, the trade groups said that they “firmly support sharing information and collaborating with government partners to address cybersecurity threats.” They supported the Cyber Incident Reporting for Critical Infrastructure Act, which covers financial services and other sectors identified under a preexisting presidential directive.
Infrastructures Identified
That template for CISA oversight of SIEs is the 16 “critical infrastructure sectors whose assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.”
Those sectors, paired with their respective sector risk management agencies, are:
- Chemical Sector – Department of Homeland Security
- Commercial Facilities Sector – Department of Homeland Security
- Communications Sector – Department of Homeland Security
- Critical Manufacturing Sector – Department of Homeland Security
- Dams Sector – Department of Homeland Security
- Defense Industrial Base Sector – Department of Defense
- Emergency Services Sector – Department of Homeland Security
- Energy Sector – Department of Energy
- Financial Services Sector – Department of the Treasury
- Food and Agriculture Sector – Department of Agriculture and Department of Health and Human Services
- Government Facilities Sector – Department of Homeland Security and General Services Administration
- Healthcare and Public Health Sector – Department of Health and Human Services
- Information Technology Sector – Department of Homeland Security
- Nuclear Reactors, Materials, and Waste Sector – Department of Homeland Security
- Transportation Systems Sector – Department of Homeland Security and Department of Transportation
- Water and Wastewater Systems Sector – Environmental Protection Agency
The Cybersecurity Solarium Commission said it was focused on “supporting a legislative proposal that would require the Secretary of Homeland Security to define a process for designating entities as systemically important critical infrastructure, with coordination from sector risk management agencies and relevant regulatory authorities. Entities so designated would be subject to higher security standards; they would also receive increased intelligence and protection to prevent disruption or compromise.”
The ABA and BPI said that they “encourage efforts to mature CISA’s capabilities and refine risk assessment models.”
Besides citing concerns about reporting complications and potential leakage of information that hackers could exploit, the associations complained of “insufficient support for operational collaboration between firms and intelligence agencies.”
Saying they would welcome more opportunity for such collaboration, they added: “Any legislation addressing national systemic risks should institutionalize operational collaboration on national security threats between firms and intelligence agencies, including clear legal authorities, guiding policies, and corresponding resourcing to support the protection of critical infrastructure.”
The ABA-BPI comment concluded by pointing to financial institutions’ “decades of experience meeting the requirements of existing systemic designations” and their record of compliance “with rigorous legal and regulatory requirements for the security and resilience of their operations . . . We have significant concerns with the SIE provision and encourage much greater dialogue and consideration of its impact on financial institutions given the complexities of our sector and myriad regulatory requirements. Legislation this important merits full consideration by relevant committees, including hearings and debate.”
Topics: Cybersecurity