
Cyberattacks present a complex, advancing danger to the global financial system, with recent breaches exposing deep-rooted vulnerabilities. Given the rapid digitization of the financial sector and the proliferation of cyber threats, any cyber event with far-reaching consequences for economic and financial stability can pose a serious risk.
Beyond idle speculation, how can risk managers measure and manage these risks in a rigorous fashion? Before answering this question, it’s important to remember that cyber risks typically exist both within and outside of a financial institution, and therefore present unique challenges.
Cristian deRitis
For example, a ransomware attack could lock a business out of its own systems, directly affecting its ability to operate. But the risks don’t end there. Customers could be the victims of identity theft (with fraudulent accounts opened in their names), and a lender in this situation must consider how to deal with a credit default resulting from a customer who has been cut off from his or her payment accounts.
Even more insidious is the threat that cybercriminals may use artificial intelligence (AI) to generate synthetic customer profiles, complete with fraudulent employment documentation and seemingly human mannerisms.
Regardless of whether an organization has secured its own systems and introduced protocols to deal with customers affected by cyber threats, they may still face exposure from their vendors. Most obvious is the reliance on cloud computing or other software service providers – but a cyberattack on a shipping company, government agency or utility might be equally disruptive to a company’s operations.
Risk managers, in short, need to develop contingency plans for a broad array of threats. How should they go about this?
From Qualitative to Quantitative Analysis
While the range of vulnerabilities is wide, the approach to managing cyber is similar to other risks. It requires an ongoing process of identifying, analyzing and evaluating varying threats.
For risk modelers, the lack of data to support a robust empirical modeling framework is a challenge. Cyberattacks are highly idiosyncratic, making it difficult to aggregate them in a statistically meaningful way. Furthermore, given the reputational or headline risks associated with ransomware and other intrusions, companies may be reluctant to report attacks in a timely or transparent manner.
Like other rare or tail events, risk teams may rely primarily on qualitative assessments of their cyber risk exposure. Business unit heads, for example, may be surveyed to identify potential vulnerabilities with a five-point scale to rank perceived probabilities and severities from “very high” to “very low.” The resulting risk matrix can help stakeholders assess the potential threats.
While a helpful first step, the qualitative approach is subject to biases, inconsistencies and data gaps. Risk modelers therefore need to pair these approaches with quantitative, scenario-based methods to provide a more meaningful and actionable analysis.
Even recognizing that quantitative data and models will be subject to revision over time, and that confidence intervals may be wide, there is greater value in estimating a $10 million expected loss exposure due to cyber threats versus a more generic statement identifying cyber as a “significant” risk. Dollar estimates enable senior leaders to make comparisons, weighing the costs and benefits of adopting various defense measures. Ultimately, this will allow them to prioritize resources to address specific vulnerabilities.
Cyberattack Contagion in the Financial System
An example of a more quantitative approach to cybersecurity is consideration of a cyberattack on key parts of the financial system. Financial institutions are prime cyberattack targets, because of their large capital positions, their reliance on software, and their interconnectivity. Indeed, the sector has suffered from numerous successful breaches in recent years, including a surge in ransomware-as-a-service that has led to highly disruptive and increasingly sophisticated attacks.
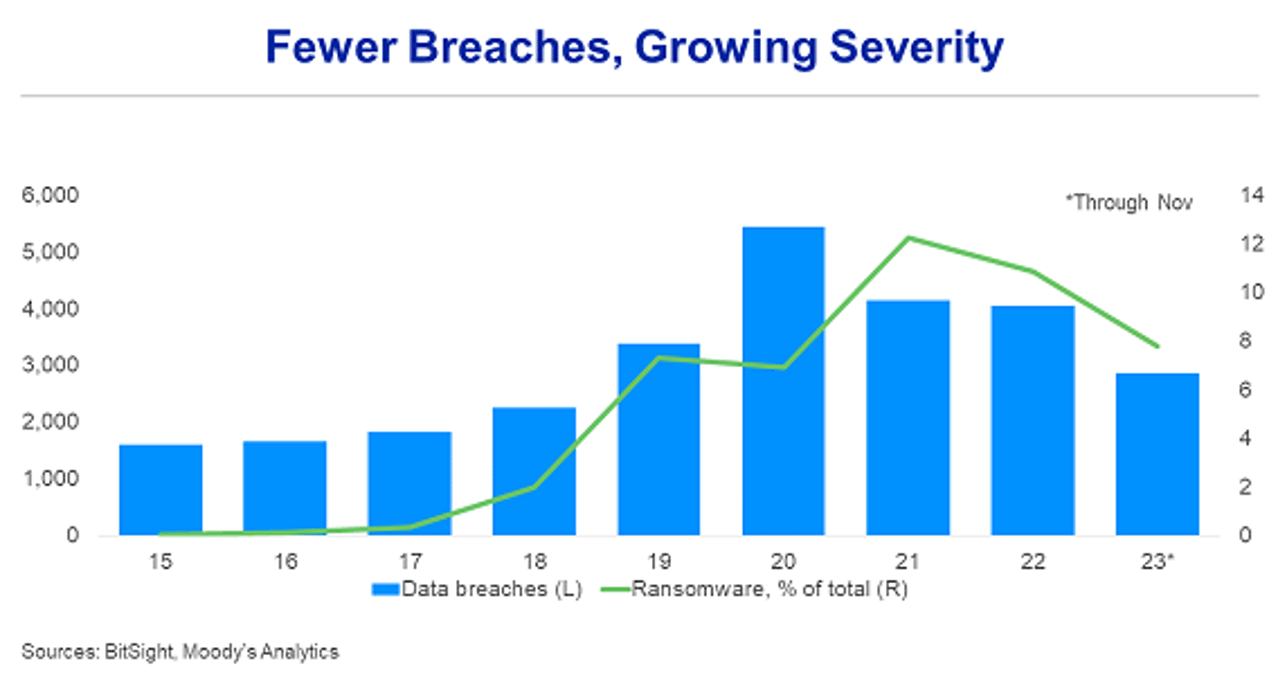
The growing severity of these breaches underscores the increased risk of future attacks. These widespread impacts are occurring despite cybersecurity investments and mandatory stress tests from regulators, such as the European Central Bank, involving simulated cyberattacks.
The rise of mobile banking apps and the ease of fund transfers, moreover, have made the possibility of a cyber-induced banking panic even more likely.
Cyber Deposit Run Scenario
Given this background, Moody’s Analytics recently developed a pair of extremely disruptive cyberattack scenarios.
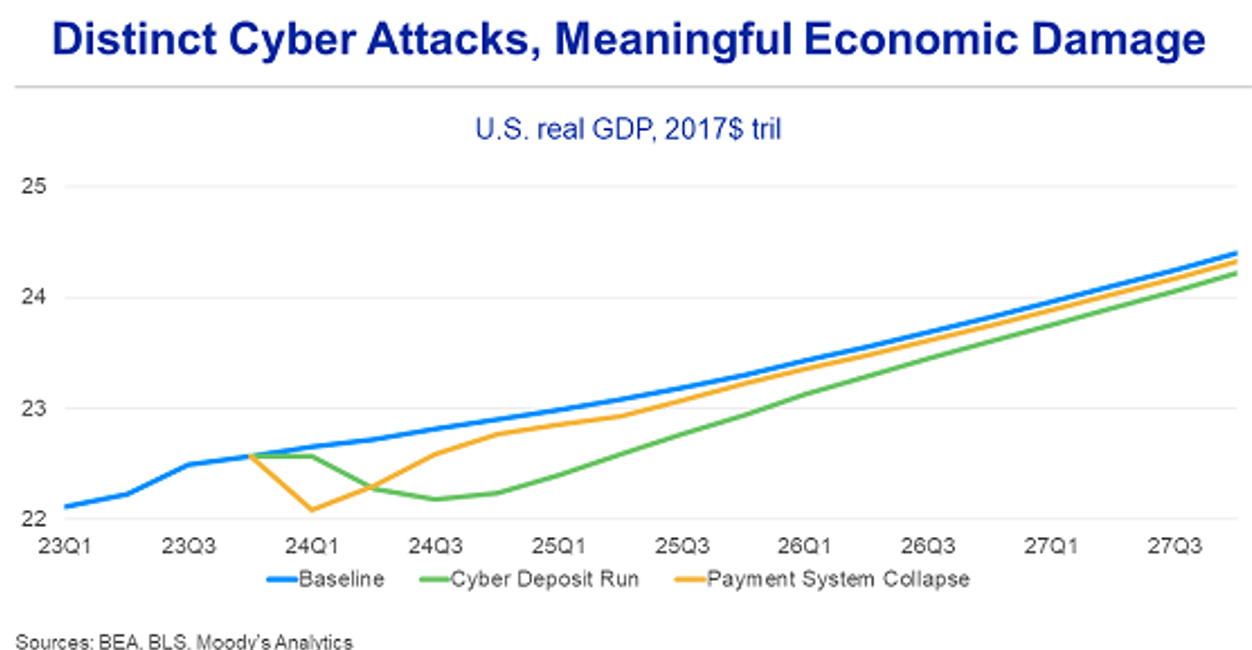
The first scenario considers a series of ransomware attacks on small and midsize U.S. banks that disrupt their internal networks – attacks that would lock depositors out of their accounts and interrupt payment services for up to 10 business days. Such a disruption would lead to a large-scale banking panic, with customers migrating from smaller banks to the perceived safety of larger institutions and money market funds.
Cybersecurity responses and enhancements at affected banks would presumably reduce the direct impact of the attacks – but would also be insufficient to restore depositor trust or broad economic sentiment. Output would drop, because consumers would pull back on spending and businesses investment retreats. Unemployment, moreover, would rise, triggering a recession.
This scenario is grounded in the cyber preparedness gaps between the largest banks and their smaller peers, which are less likely to conduct advanced cyber-defense practices. It also takes into account security requirements for third-party vendors, which may vary in stringency.
Payment System Collapse Scenario
The second scenario examines the impact of a cyberattack on the automated clearing house (ACH) network, which would cause significant disruption to the retail payments system for three weeks – including payroll direct deposits, electronic bill payments, and peer-to-peer payment services such as Venmo and PayPal.
Under this scenario, we assume that credit card networks would fear contagion and would therefore suspend access to their systems for a period of time, forcing a mass migration from electronic payments to checks and cash.
An ACH attack would cause immediate economic disruption, affecting household incomes, consumer payments and credit markets. This would lead to a sharp economic downturn, as businesses curtail operations and consumers increase their precautionary savings. Fear would take over, as households and businesses would worry about the safety of their deposits and as banks would be forced to ration cash withdrawals.
The initial drop in output would be greater than in the first scenario, considering frictions on business and consumer spending and fears of permanent loss of access to income and savings. Recovery would be more rapid than in the first scenario, since we’d surely see the restoration of the ACH network, emergency rate cuts by the Federal Reserve, and legislative relief measures. However, lingering consumer sentiment issues would still slow the pace of recovery.
Parting Thoughts
As with any scenario-planning exercise, it can be useful to quantify the potential effects of a cyber shock – but some of the greatest value for a risk team comes from working through the process. A simulation can uncover additional considerations and identify actions that can mitigate the fallout. While the cyberattack scenarios considered here would push the economy into a deep recession, they may not fully capture the knock-on effect of a panic on an individual bank or business.
Cybersecurity merits the full attention of risk professionals, given how highly interconnected households and businesses are with the broader financial system. Even if a business buttons up its own cybersecurity measures, it may still be vulnerable to cyberattacks on its customers or vendors. The macroeconomic consequences of a large-scale attack on critical digital or physical infrastructure could have significant ramifications that risk teams need to consider.
While IT departments bear much responsibility in defending against cyber threats, risk teams can support decision making and resource prioritization by collecting empirical data and by providing a more quantitative approach to assessing cyber threats.
Cristian deRitis is the Deputy Chief Economist at Moody's Analytics. As the head of model research and development, he specializes in the analysis of current and future economic conditions, consumer credit markets and housing. Before joining Moody's Analytics, he worked for Fannie Mae. In addition to his published research, Cristian is named on two U.S. patents for credit modeling techniques. Cristian is also a co-host on the popular Inside Economics Podcast. He can be reached at cristian.deritis@moodys.com.
Moody’s Analytics recently tackled the topic of cybersecurity in a podcast and a research report.
Topics: Data