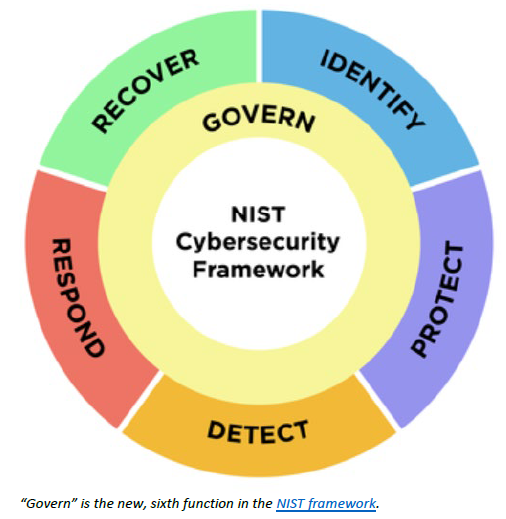
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF), which for nearly a decade has guided finance and other critical infrastructures’ preparedness for and responsiveness to cyber threats, is being revised to address all organizations of any size and bolstered with a new governance “pillar.”
The draft of CSF 2.0, which NIST published in August for a three-month comment period, is billed as the framework’s first complete makeover. The U.S. Department of Commerce agency said there is “widespread agreement that changes are warranted to address current and future cybersecurity challenges and to make it easier for organizations to use the framework.”
To the five main functions, or pillars, in the CSF – identify, protect, detect, respond and recover – NIST added “the govern function, which covers how an organization can make and execute its own internal decisions to support its cybersecurity strategy. It emphasizes that cybersecurity is a major source of enterprise risk, ranking alongside legal, financial and other risks as considerations for senior leadership.”
Implicit in “govern” are “organizational context; risk management strategy; cybersecurity supply-chain risk management; roles, responsibilities and authorities; policies, processes and procedures; and oversight,” as outlined in NIST’s public draft. It added: “Focus on people, process, and technology expanded throughout the implementation of the framework.”
Related NIST Activities
It points out that the program relates to “other frameworks and resources,” including such titles as the NIST Privacy Framework, Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations, the Integrating Cybersecurity and Enterprise Risk Management series, and the NIST Artificial Intelligence Risk Management Framework released last January.
Also on the AI front, NIST provides administrative support to the National Artificial Intelligence Advisory Committee (NAIAC) and was assigned a standard-setting role in the Executive Order on Safe, Secure, and Trustworthy Artificial Intelligence. One of the October 30 White House order’s directives is for the Secretary of the Treasury to issue within 150 days “a public report on best practices for financial institutions to manage AI-specific cybersecurity risks.”
NIST’s Post-Quantum Cryptography project, addressing potential future data-security vulnerabilities, is working toward publication of a standard in 2024.
Future Adaptability
More than five years since its CSF version 1.1 update, NIST is “trying to reflect current usage of the Cybersecurity Framework, and to anticipate future usage as well,” Cherilyn Pascoe, CSF lead developer, said in August. The framework “was developed for critical infrastructure like the banking and energy industries, but it has proved useful everywhere from schools and small businesses to local and foreign governments. We want to make sure that it is a tool that’s useful to all sectors, not just those designated as critical.”
Cherilyn Pascoe is director of NIST’s National Cybersecurity Center of Excellence (NCCoE).
The CSF represents a common language on cybersecurity imperatives across businesses, says Robert Kolasky, who was the founding director of the Cybersecurity and Infrastructure Security Agency (CISA) National Risk Management Center and is now senior vice president of critical infrastructure at Exiger.
“Banks are on the leading edge of framework adoption, and it has been incorporated into cyber risk management plans and regulatory requirements,” Kolasky notes. “The increase in prominence for governance has the likely impact of raising the level of accountability to bank and other corporate leadership for cybersecurity. Coupled with the new [Securities and Exchange Commission] rules for publicly traded companies, the message is clear: cyber is a board-level issue.”
Onus on the C-Suite
The govern function is seen as elevating the importance of cyber risk management in business and compliance outcomes, signifying “that cybersecurity is not just a technical matter, but also a governance and organizational issue,” states Fayyaz Makhani, global security architect at VikingCloud. “It emphasizes that effective cybersecurity requires not only implementing technical safeguards, but also having clear policies, procedures and roles in place to manage and govern cybersecurity risks.”
“Govern” and its focus on risk management gain prominence that they didn’t have when previously subsumed within the “identify” pillar. Kolasky sees this underscoring its enterprise-level status, deserving corporate leadership’s attention.
Exiger’s Robert Kolasky: Message to the boardroom.
“The framework was always intended to be a tool to help CISOs [chief information security officers] and their peers communicate in the boardroom and C-suite, but the governance addition flips the paradigm a bit,” Kolasky explains. “It is intended to send the message that the C-suite needs to drive framework adoption. In terms of what it means for the overall state of cybersecurity, I think it is just reinforcing the idea that cyber risk is enterprise risk, and that security fails when done in isolation of corporate priorities.”
“Organizational leadership should take responsibility for cybersecurity risk decisions and cultivate a risk-aware culture,” Makhani states.
Voluntary and Popular
Although CSF prescriptions are voluntary, the document has gained adherents across sectors and geographies such that the expansion of its scope beyond critical infrastructure is in a sense already accomplished, observes Gartner distinguished VP analyst Katell Thielemann. “Many organizations globally use the CSF as an organizing framework, whether they align to critical infrastructure or not. The addition of the governance function will further help organizations adopt it as a comprehensive framework with leadership buy-in and continuous management.”
Highly regulated industries such as financial services tend to have well-established cybersecurity programs with governance components, and these may draw from guidance from NIST or other frameworks, according to Kris Lau, an ACA Aponix managing director. Agencies such as the SEC and Federal Trade Commission cite the CSF in regulatory guidance, reinforcing its benchmark-setting role.
Kolasky regards the framework as evolutionary, in a sense catching up to best practices already adopted in the financial sector, which is widely seen as one of the most experienced and advanced. Kolasky says.
“Alignment with Business Goals”
As an example of refining existing functions and practices, “organizations should involve key stakeholders and establish and communicate clear objectives for managing cybersecurity risks, ensuring alignment with business goals,” Makhani says.
He also advises “developing strategies and processes for managing cybersecurity risks within the supply chain, including third-party assessments and monitoring”; defining and communicating “risk appetite and tolerance in the context of the business environment”; and ensuring “that cybersecurity risk management is integrated into the broader enterprise risk management framework.”
“A strategic direction should be established and communicated, outlining risk response options, including risk transfer mechanisms, investments in mitigations, and risk acceptance,” Makhani adds.
In line with enterprise risk management principles, the guidelines recommend systematic communication and cooperation between business lines and security teams.
Gartner’s Katell Thielemann: Each implementation unique.
“I would expect organizations that already leverage the CSF to expand the maturity of their governance models and update risk assessments to take into account their supply chains,” Thielemann says. “And I would expect organizations that are not leveraging the CSF to take another look, as the more comprehensive framework might help them organize risk at the enterprise level.
“But we should also note that the flexibility built into the CSF originally, and kept under this revision, means that the guidance for managing cyber risks is high-level,” the Gartner analyst continues. “Each organization’s implementation of the framework will be different, because everyone’s risks are unique, whether we’re talking about different threats, vulnerabilities, risk tolerances or ranges of impacts.
Impact on Individuals and Teams
The revised CSF is likely to affect security teams’ involvement in cyber risk management, Makhani says. That means closer collaboration with other parts of the organization, including leadership, to ensure that risk management strategies are effectively implemented and assessed. They may also be responsible for monitoring and reporting on compliance with new governance directives derived from the framework.
Security teams will have to develop strategic leadership qualities in addition to the tactical security-control skills that they are more traditionally known for, Thielemann maintains.
It is important to stress the need for ongoing awareness and training within an organization to ensure that all employees are on the same page of understanding and implementation, Makhani says. It is essential for all to be vigilant as new technologies such as generative AI emerge, and to be prepared to adapt to current and future changes in the threat landscape.
Topics: Cybersecurity