
When a power blackout hits, people worry about spoiled food and other inconveniences. At businesses, continuity plans have to kick in. The Department of Homeland Security has to contemplate if this is “the one” - a terrorist or nation-state attack on critical infrastructure.
Energy is one of DHS's 16 sectors - others include communications, financial and transportation - designated as critical infrastructures, with various interdependencies, whose “incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.”
Critical infrastructure protection is a national security and policy concern, but the legislative record has lately been spotty at best. The polarized and unproductive Congress, although able to pass general-purpose legislation like the Cybersecurity Information Sharing Act of 2015, has failed to take action on what is, according to broad consensus, a particularly fragile link in the infrastructure chain: the electric grid.
Seen as vulnerable to malware and other cyber attacks, physical threats, sun flares and electromagnetic-pulse (EMP) weaponry, the grid would be shored up by Senate bill 1846, the Critical Infrastructure Protection Act, (CIPA). Amending the Homeland Security Act of 2002, the bill would direct DHS to take on tasks related to intelligence, analysis and protection of the grid.
Sponsored by Senator Ron Johnson, Republican of Wisconsin and chair of the Senate Homeland Security and Governmental Affairs Committee, S. 1846 has been languishing in committee since November 2015 and in all likelihood will be the third such “grid bill” to die when the current Congress officially adjourns.
“Our nation's critical infrastructure sectors are not only lifelines in the integrated system, they are also crucial to our country's economic stability and national security,” Sen. Johnson, who was re-elected on November 8, stated in May 2016.
A corresponding House bill, HR 1073, passed with unanimous, bipartisan support in August 2015. Its lead sponsor, Representative Trent Franks, Republican of Arizona, has said CIPA “would protect the national electric grid from man-made and natural threats that could cause a protracted blackout of the life-sustaining critical infrastructures - communications, transportation, business and finance, food and water.”
Incidents on the Rise
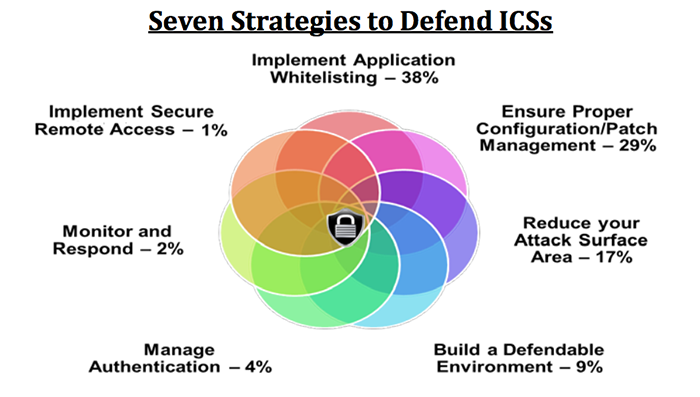
The DHS collaborated with the Federal Bureau of Investigation and National Security Agency on a December 2015 report, Seven Steps to Effectively Defend Industrial Control Systems, saying that “it's not a matter of if an intrusion will take place, but when.”

“Cyber intrusions into U.S. critical infrastructure systems are happening with increased frequency,” according to the document, which said 295 such industrial control system (ICS) incidents were reported in fiscal year 2015. One example given was “a Stuxnet infection at a power generation facility. The root cause of the infection was a vendor laptop.” (Stuxnet was the malware involved in a 2009-'10 attack on Iran's nuclear power program that is widely regarded as an incident of cyber warfare.)
The agencies said that had grid owners “implemented the strategies outlined in this paper,” 98% of incidents that ICS-CERT [the Industrial Control System Cyber Emergency Response Team] responded to in fiscal years 2014 and 2015 “would have been prevented. The remaining 2% could have been identified with increased monitoring and a robust incident response.”
In January 2016, the Federal Energy Regulatory Commission proposed that all grid operators record and report such events.
A source within a government security entity, who agreed to speak on condition of anonymity, gave this scenario of what keeps them awake:
North Korea is capable of positioning a ship at a point in the Pacific Ocean from which an on-board rocket launches, exploding its nuclear payload into the upper atmosphere at a mid-point above the grid, such as Kansas. The electromagnetic pulse set off by the strike burns out a piece of connective equipment common across the grid, disabling most or all of the power network. Most of the country is plunged into darkness. All electric stops, once available gas for generators is exhausted, and fuel pumps cease without electric power. Air as well as ground transport comes to a halt. Months pass and food supplies dwindle as local stocks go unreplenished, and the country, hungry and angry, awaits the grid's replacement parts to come by ship - most likely from manufacturers in South Korea.
Alarm about EMP
Security watchdogs like the nonprofit Foundation for Resilient Societies (FRS), co-founded by engineer Steve Mott and entrepreneur Thomas Popik, and the Task Force on National and Homeland Security attempt to raise awareness of grid vulnerabilities.
The task force's executive director is Peter Vincent Pry, a former Central Intelligence Agency analyst and chief of staff of the Congressional Electromagnetic Pulse Commission, who also held a key role in the Congressional Commission to Assess the Threat to the U.S. from EMP and is the author of “Apocalypse Unknown: The Struggle To Protect America From An Electromagnetic Pulse Catastrophe.” The congressional EMP commission is chaired by William R. Graham, former chair of President Reagan's General Advisory Committee on Arms Control from 1982 to 1985.
Pry has been a frequent co-author with Henry F. Cooper on EMP vulnerabilities and possible protective measures. Cooper, who has a Ph.D. in mechanical engineering from New York University and was the first civilian director of the Strategic Defense Initiative Organization created by President Ronald Reagan in 1984, is a director of the FRS.
In an April 30, 2015, Wall Street Journal opinion article, “The Threat to Melt the Electric Grid”, Cooper and Pry noted the Pentagon's decision to “go back underground,” that is, move some critical operations of its North American Aerospace Defense Command (Norad) from Peterson Air Force Base in Colorado to the nearby, naturally EMP-hardened Cheyenne Mountain complex. The authors saw the move as an indication of Norad's concern for EMP vulnerability.
The authors also asserted that North Korea had mobile ICBMs armed with nuclear warheads that can strike the U.S. - a point still being debated. According to the transcript of an April 7, 2015, briefing, the Norad Commander, Admiral William Gortney, said that North Korea can put “a nuclear weapon on a KN-08 and shoot it at the homeland.” He added, “We haven't seen them test the KN-08 yet, and we're waiting to do that.”
Asked by a reporter if he was being overly cautious, rather than basing his statement on access to facts, Gortney replied, “No, I think it's a prudent decision by my assessment of the threat, and the threat to the nation.”
Although Gortney said that the U.S. can defend itself from North Korean and, if necessary, Iranian missiles, Cooper and Pry said that is the case only if the attack comes from the northern skies. “Former Reagan administration officials warn that the U.S. is unprepared to cope with nuclear EMP strikes . . . if their missiles' trajectory takes a southern route,” they claimed.
Pre-emptive Posturing
In a new monograph series, The Long Sunday, Pry portrays world leaders as leaning toward or favoring a surreal pre-emptive nuclear EMP strike against an undeclared enemy. He cites chilling first-strike philosophies of global powers, while laying out scenarios and making arguments for seizing a nuclear first-strike advantage.
“The Long Sunday” refers to the time between Election Day in November 2016 and Inauguration Day in January 2017, when Pry suspects enemies might perceive U.S. weakness in the midst of changing administrations.
Pry quotes former CIA director R. James Woolsey: “Because EMP destroys electronics directly, but people indirectly, it is regarded by some as Shariah-compliant use of a nuclear weapon. Passive Defense and other Iranian military writings are well aware that nuclear EMP attack is the most efficient way of killing people, through secondary effects, over the long run.”
Pry interjects here his alternative to a nuclear war: reviving the Strategic Defense Initiative. “SDI could make unnecessary the dangerous revolution in military technology now under way developing offensive cyber and EMP weapons for striking first," he writes. "SDI could replace these destabilizing offensive technologies with stabilizing defensive technologies, and make the world a much safer place.”
“The call for cyber and nuclear (EMP) pre-emptive strikes is from the Obama administration's Department of Defense in testimony before Congress,” Pry said in an email. “I only very reluctantly agree with these recommendations because the Obama administration has failed to implement the better, safer alternatives...”
Pry and his like-minded colleagues consider Donald Trump “far more likely than Hillary Clinton to harden the grid and other critical infrastructures, strengthen national missile defenses, and revive President Reagan's Strategic Defense Initiative.” Trump has been advised by Woolsey, Newt Gingrich and others “who understand the EMP threat and have advocated the above solutions.”
Flawed Regulatory Framework
The grid's patchwork oversight structure - 10 power markets covering the U.S. and parts of Canada, owned and managed by a tangle of government, private industry, and public/private entities with varying budgets and motivations - is a major target of critics.
The Federal Energy Regulatory Commission (FERC) was created in 1977 under the U.S. Energy Policy Act to oversee the interstate transmission and pricing of energy resources. In 2006, FERC named the North American Electrical Reliability Corporation (NERC) as the government's Electrical Reliability Organization (ERO), giving NERC regulatory power over these markets. NERC's authority to audit power companies and levy fines for non-compliance comes from FERC.
Although FERC and Canadian provincial governments retain the power of review and audit of NERC, NERC has the authority to write rules and standards aided by industry expertise.
It is that industry input that critics have seized upon. U.S. investor-owned utilities comprise 70% of the electric power industry. Critics charge that NERC, with an equal percentage of publicly-owned utility members, is more deferential to public shareholders than to the public interest of cyber protection.
In an April 20, 2015, letter to the Senate Energy and Natural Resources Committee, the Foundation for Resilient Societies said the NERC delays proposing reliability standards or will “propose weak reliability standards that will protect its utility members but not protect the public interest,” thereby subverting the “specific intent of Congress on grid cybersecurity” by failing to comply with provisions of the Energy Policy Act of 2005.
FRS sees outages like one affecting the Washington, D.C., area last year as demonstrating that the grid around the “nation's capital and elsewhere remains vulnerable to cascading outages despite federal efforts to establish a system of mandatory reliability standards since the 2003 Northeast blackout.”
Internet Insecurity
FRS is particularly concerned that utility communications are not sufficiently protected. A primary point of weakness is the increasing use by utilities' engineers of “the public Internet for sending control signals to equipment dispersed over large geographic areas,” wrote FRS chair Popik.
FRS puts ultimate blame at the feet of NERC's regulator, FERC. NERC failed to adopt any of the cybersecurity standards called for by the Energy Policy Act - over a seven-year period, Popik contends. Yet FERC approved NERC's standards as “in the public interest,” he wrote.
He singled out the April 2013 sniper attack on the Metcalf substation in San Jose, California, in which AK-47s were used and 17 transformers were shut down. Twenty three days later, a NERC committee recommended eliminating a physical security standard that was in development. And, NERC declared FERC directives for sabotage and the reporting of physical threats “no longer needed,” according to Popik. Regardless, NERC's board of trustees ratified the cancellation of the physical security project the following October.
Popik credits news accounts and a mandate issued by FERC for NERC's reversing its decision and producing a reliability directive within 90 days. Otherwise, he wrote, “there would be no physical security standard at all.”
Ukraine Attack
As grid incidents increased domestically, the U.S. mounted a response to a crippling attack on Ukraine's electric grid in December 2015. At the invitation of the Ukraine government, the U.S assembled an interagency team, with representatives from the National Cybersecurity and Communications Integration Center (NCCIC - ICS-CERT), U.S. Computer Emergency Readiness Team (US-CERT), Department of Energy, FBI and NERC. Ukraine managers “worked closely and openly with the U.S. team and shared information to help prevent future cyber attacks,” according to the U.S. agencies' February 2016 report, Cyber Attack Against Ukrainian Critical Infrastructure.
In April 2015, FRS criticized NERC for not waiting for those findings and, just 29 days after the Ukraine blackout, deeming the NERC cybersecurity standards to be “in the public interest.”
“The Ukraine blackout shows these standards are a false assurance, principally providing liability protection for utilities, but meager protection for the American public,” FRS's Popik said in an appeal of that decision. “In fact, if Ukraine's electric utilities had followed all of North America's standards for grid cybersecurity, the December cyber attack still would have succeeded - a conclusion all the more troubling considering the BlackEnergy family of malware used as the cyber-weapon of choice in Ukraine is also pervasive in computer systems of North American utilities.”
In a January 28, 2016, FERC hearing on supply chain risk management, W. A. (Art) Conklin, associate professor and director of the Center for Information Security Research and Education at the University of Houston, raised a concern about the grid's Internet dependency. “Everything is eventually connected to everything,” he said. “That's how malware gets to where malware wants to get.”
Gap in Preparedness
In a February 29, 2016, commentary for Forbes, Keeping the Lights On: Cybersecurity and the Grid, Conklin concluded not only that a Ukraine-like denial-of-service attack could happen here, but also went into why it could have worse consequences.
“Here in the U.S. as well as elsewhere, malicious malware has been found waiting for a signal to cause damage,” Conklin wrote. “Our electric grid is now interconnected to the Internet, and all of the problems and issues we see with cyber criminals and cyber spies applies to the reliability of our grid.”
“The same attack used in the Ukraine would not be stopped by our regulations,” which Conklin called “a broken and incomplete regulatory framework.
“It would be much harder for us to recover because of our greater dependency on interconnected automation.”
Investigators were impressed by the time the Ukraine hackers invested, Kim Zetter reported in Wired magazine. “Over many months they conducted extensive reconnaissance, exploring and mapping the networks,” Zetter wrote. Authorities have theorized that the dozens of attacks on U.S. substations may be preludes to something much bigger.
Meanwhile, back on Capitol Hill, promoters of the CIPA bill say it would strengthen FERC's control over NERC and put muscle behind efforts to harden the grid. There are no funding requests in CIPA, its backers say, just requirements and standards. As Rep. Frank's military legislative assistant, Andrew P. Braun, sees it, that leaves only political motives to blame for not passing the act.
With Republican Senator Ron Johnson up for re-election, “the Democratic party just doesn't want him to have any legislative victories,” Braun says. Efforts to change the status quo are “kind of bought out by folks in the industry who don't want to change anything.”
Requests for comment from the Democratic side went unanswered.